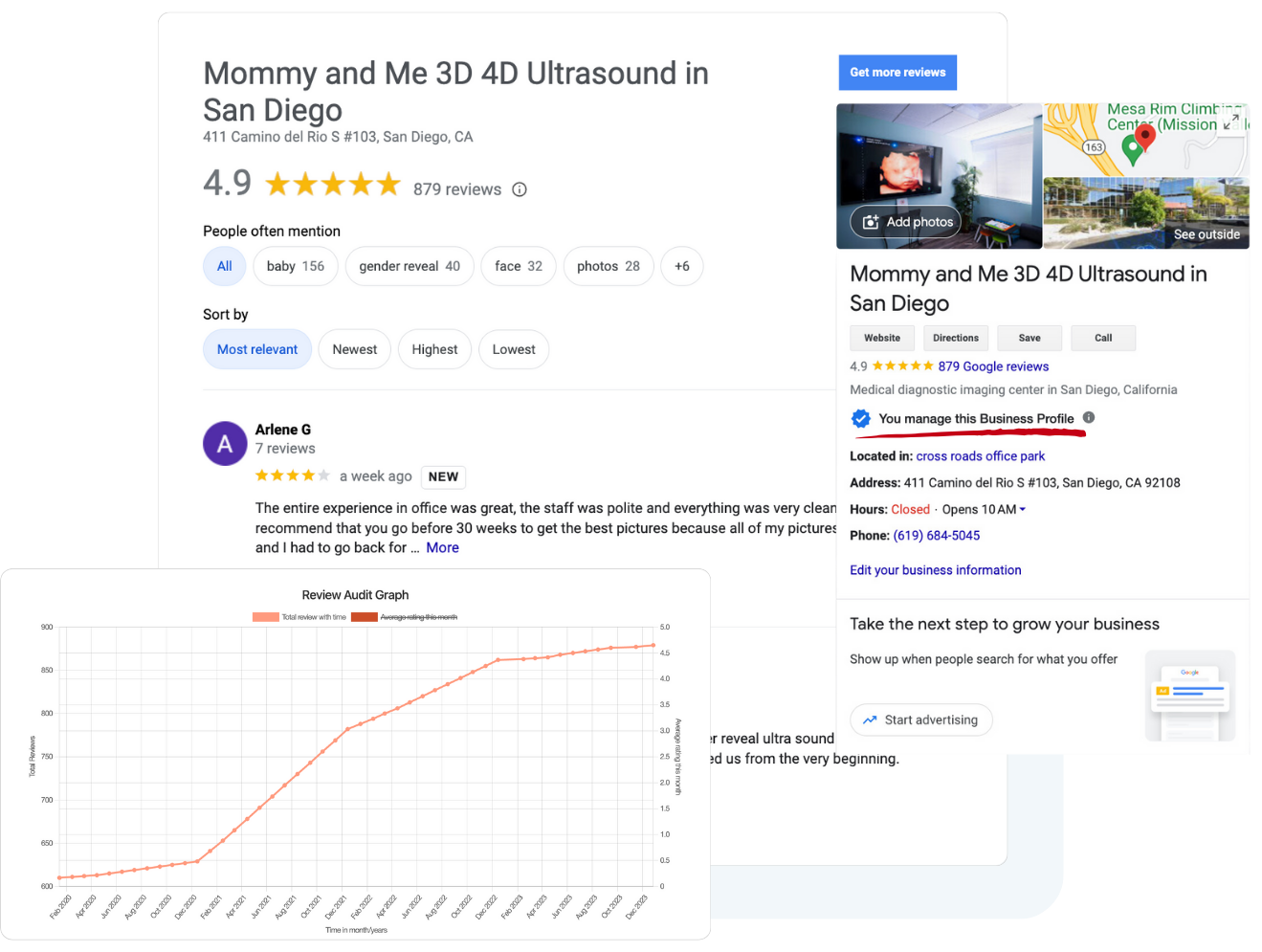
Map Ranking
We help local businesses rank higher on Google Maps, get more reviews, and expand their territory (be on multiple cities, even when your potential client is farther than 10 miles away).
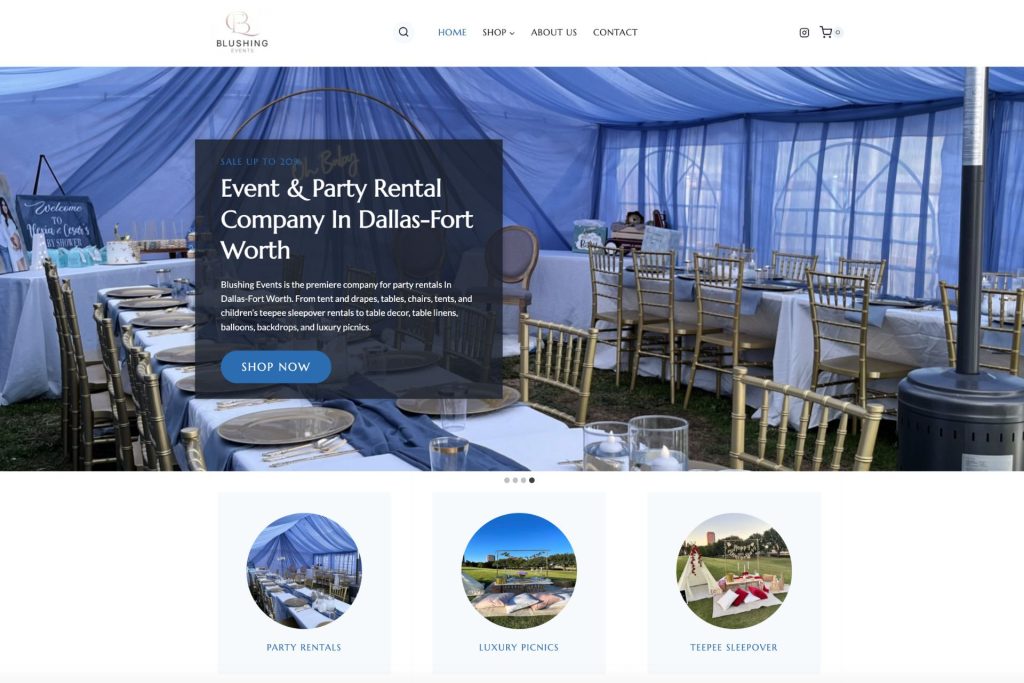
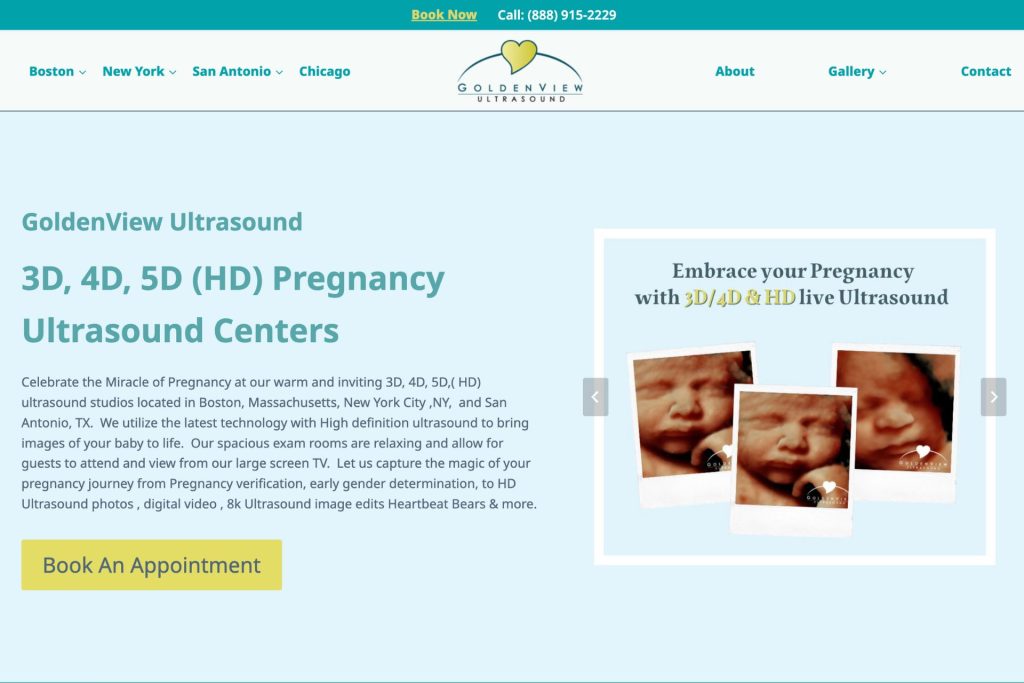
Rank Higher on Google Maps
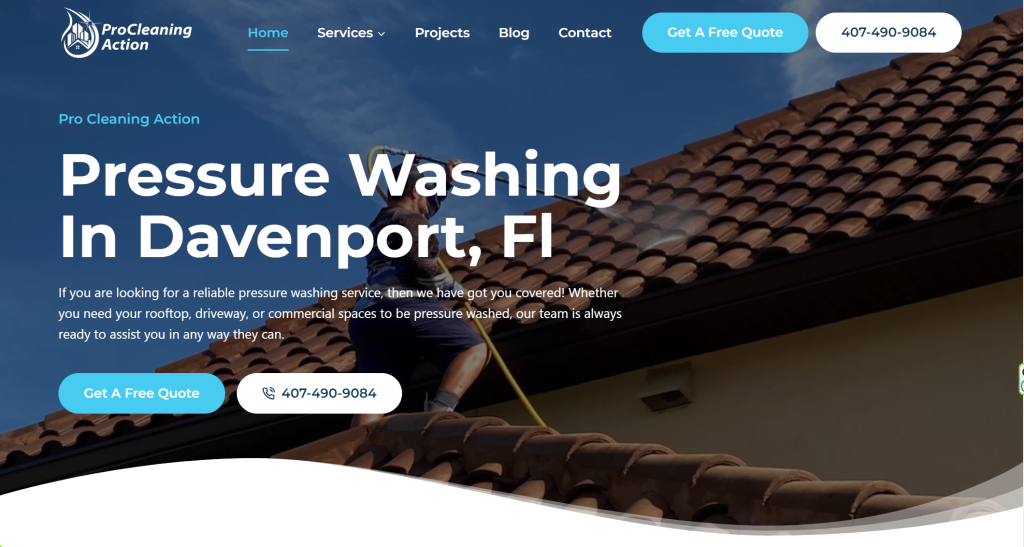
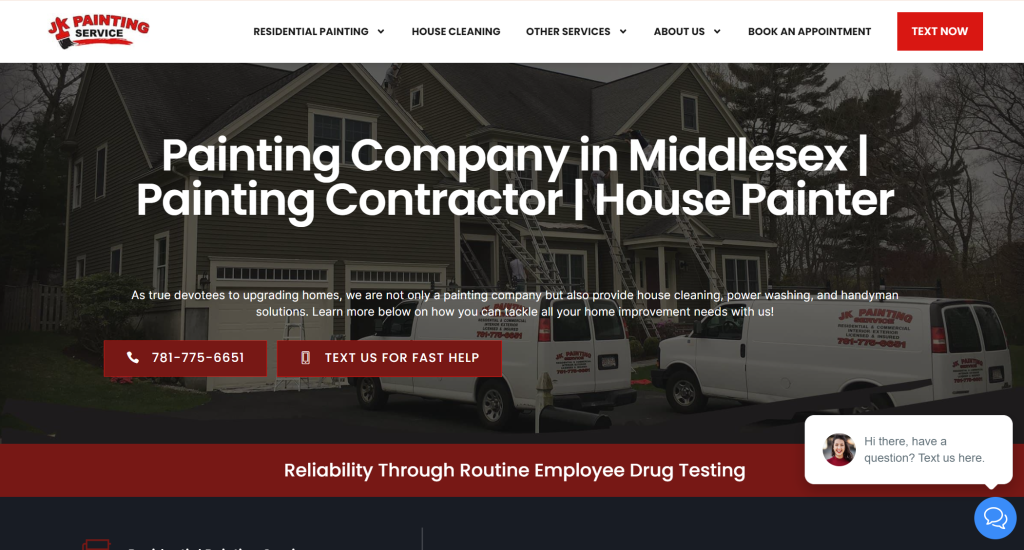
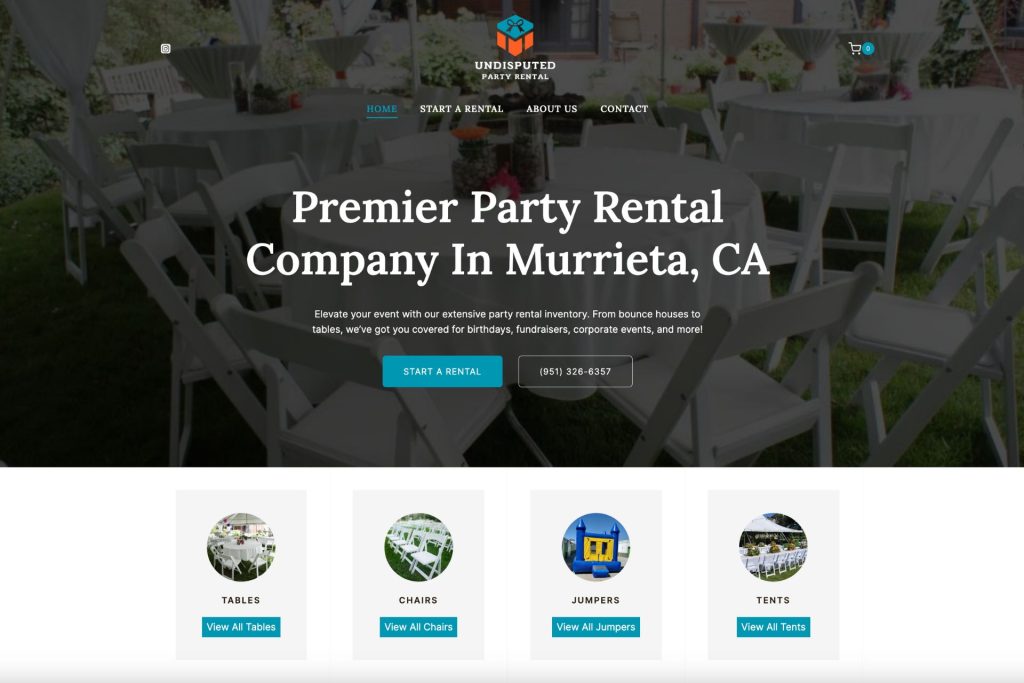
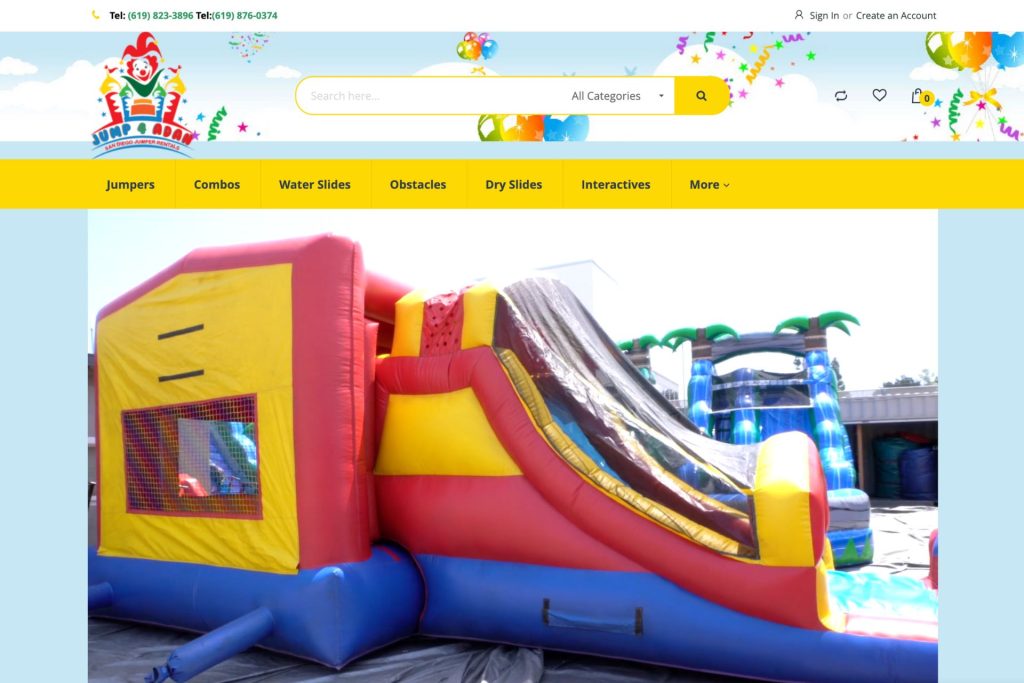
Local SEO starts with a fully optimized and managed website and Google Business Profile. We understand Google’s algorithm and optimize the features of your online presence that influence your rankings and conversions.
Territory Expansion
People search on Google for businesses like yours every single day, but they may not find you if they are more than 10 miles away. Map Ranking will help you rank higher, and in more cities around you so that you can capture more new customers.

Get More Reviews
Reviews are critical to increasing both rankings and conversions. Map Ranking’s automated review generation software will help you generate a new 5-star review every single time that you have a happy client.
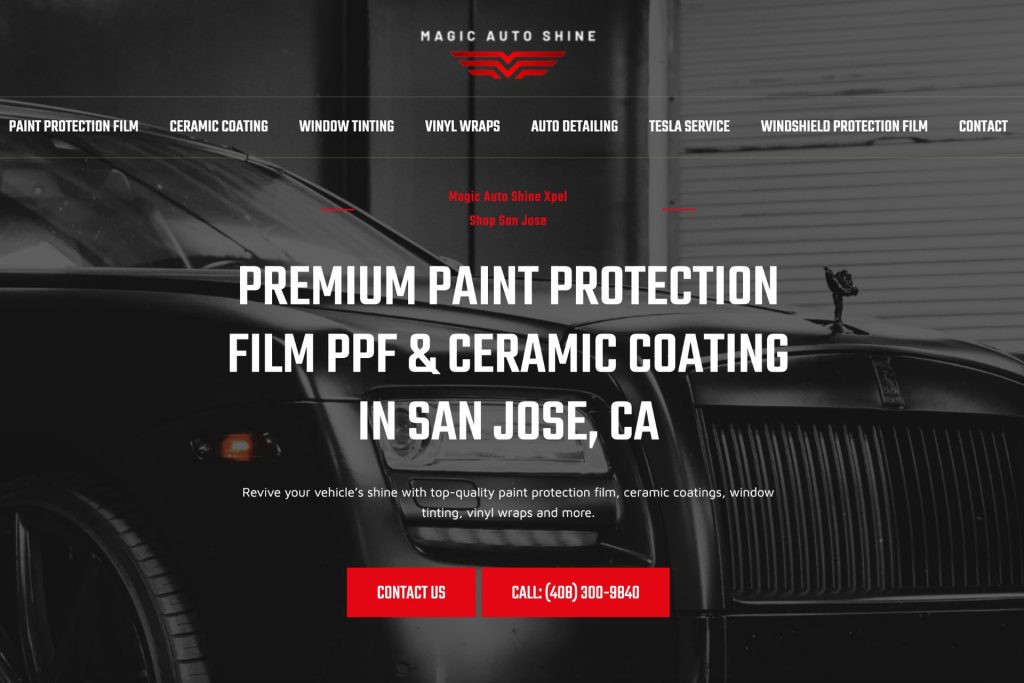
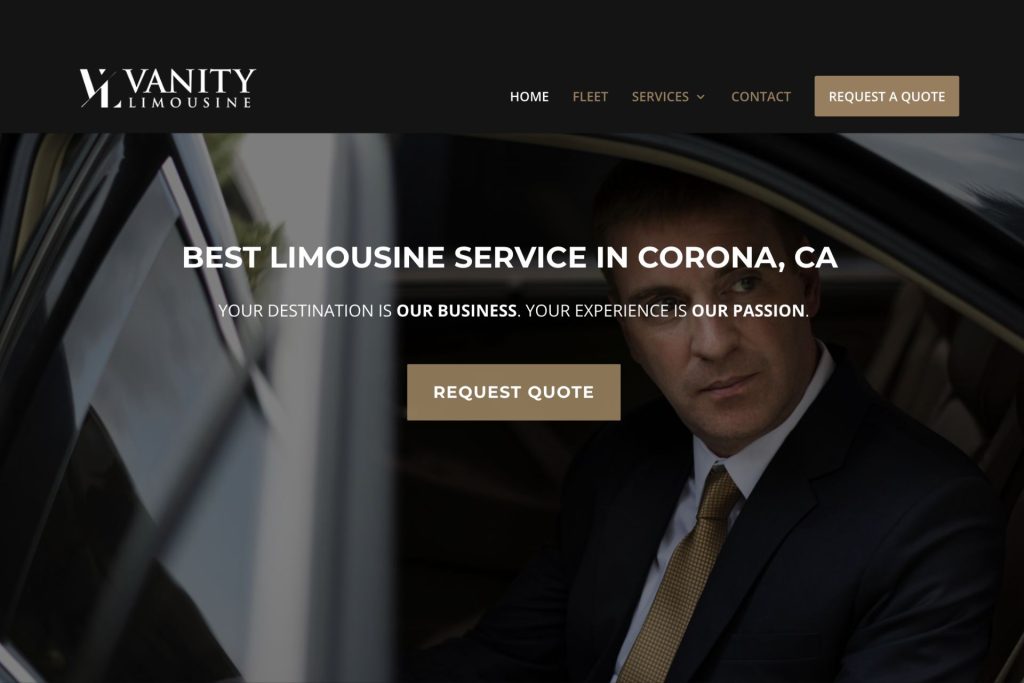
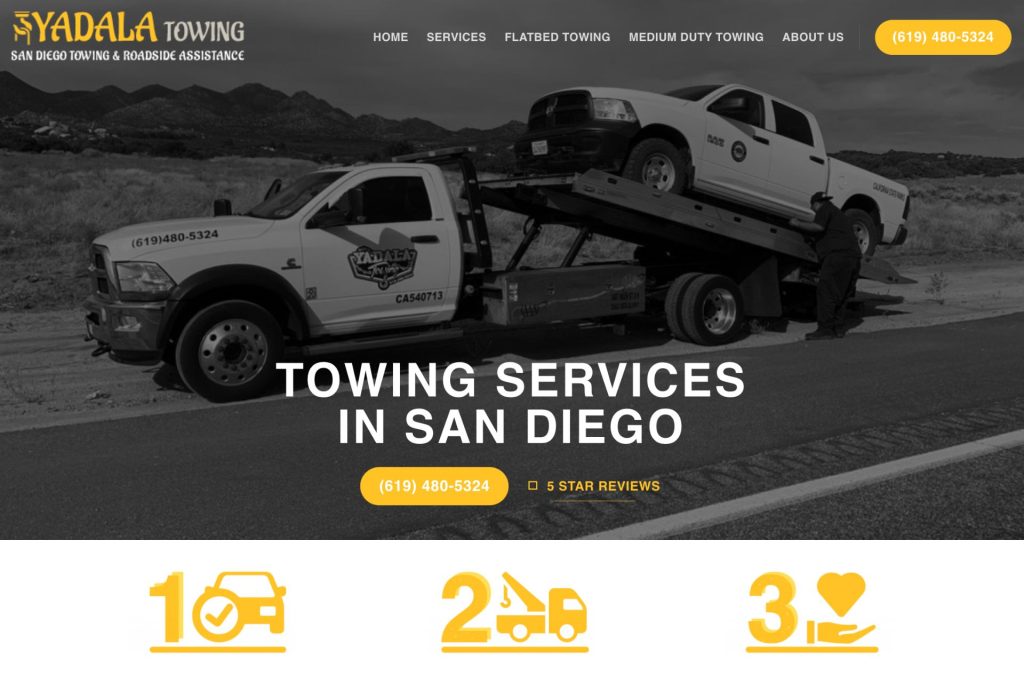
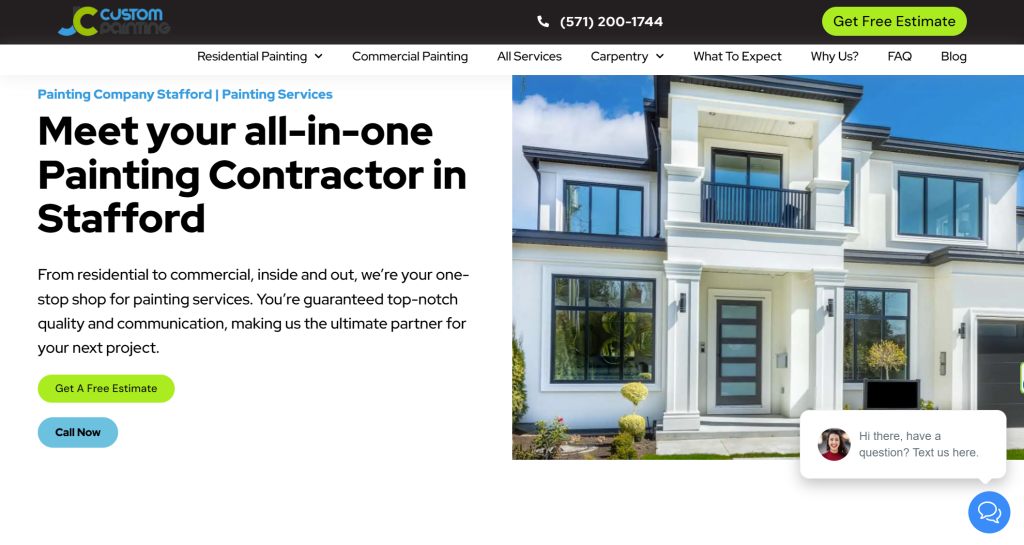
Map Ranking Web Design Services
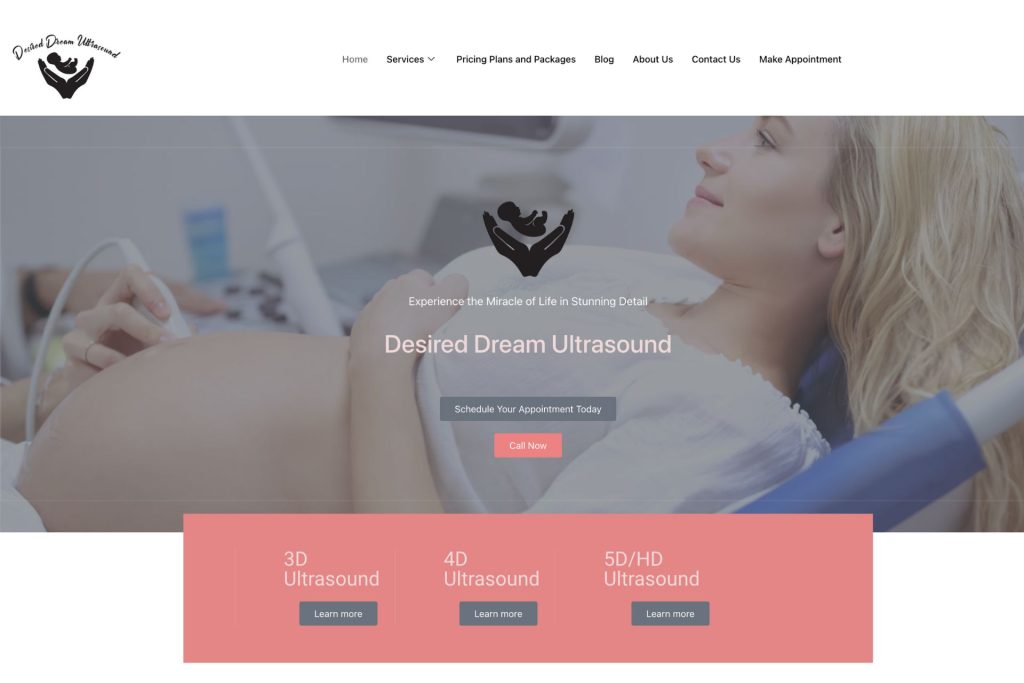
Websites that will create instant impact. Customers and consumers shop with their eyes first. Its very important to have a professional and modern site for your business.
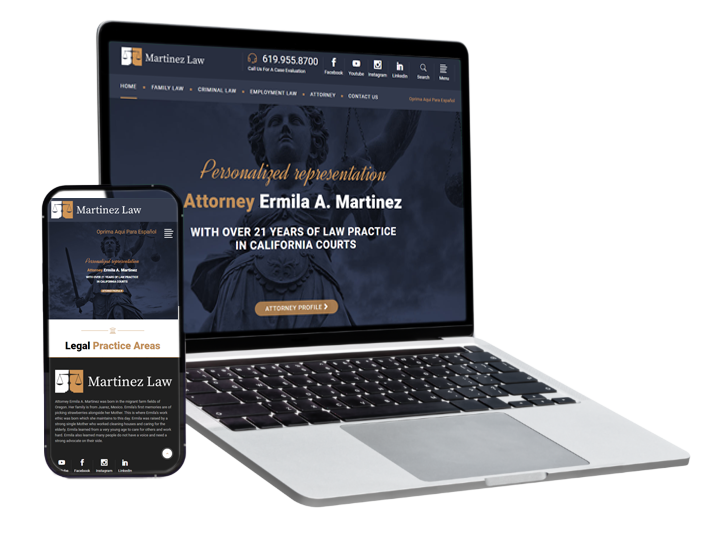
We Create Websites That Convert
Create a professional and mobile responsive website or landing page that converts like crazy.
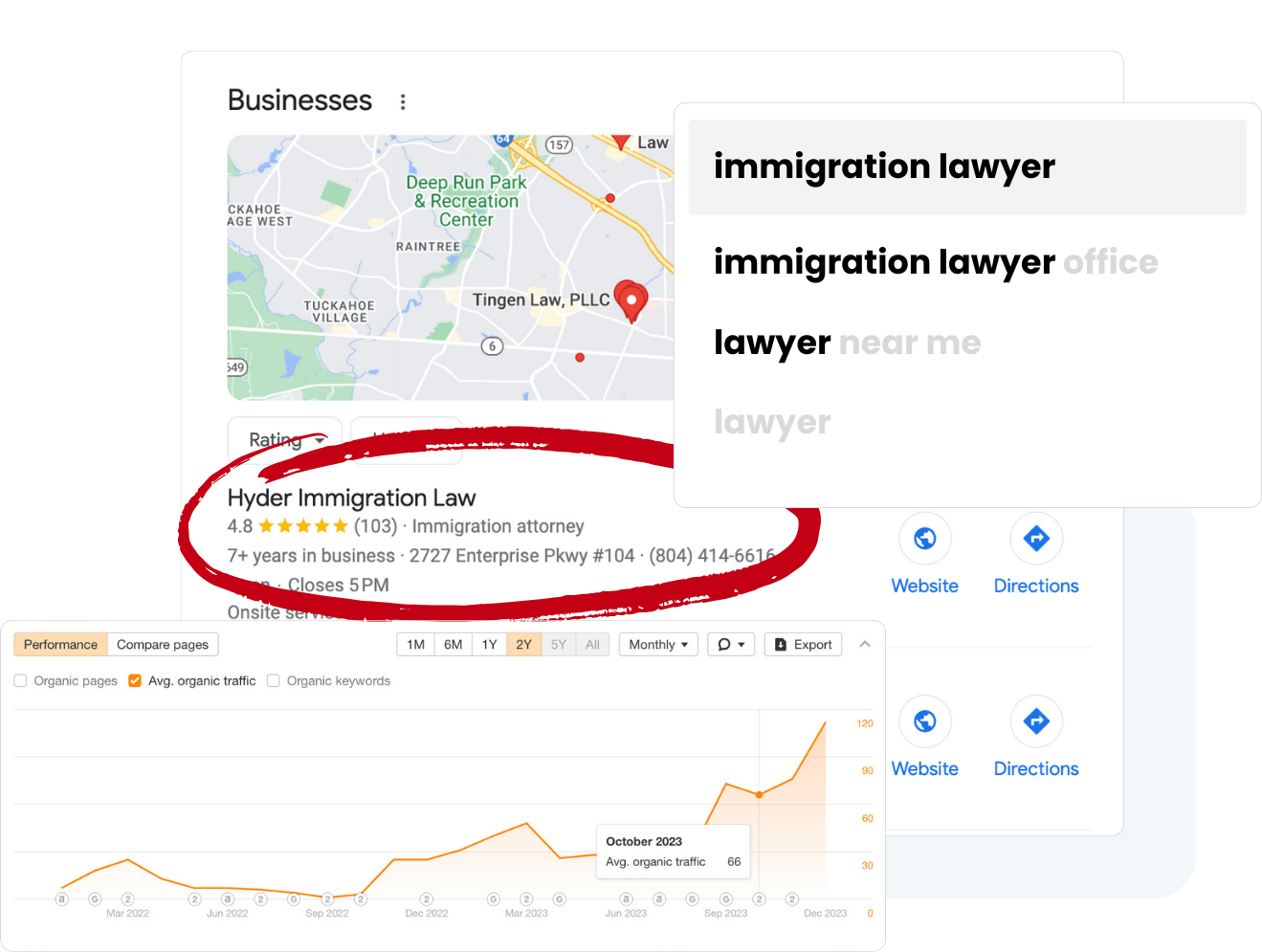
Rank Higher Google Maps
Unlock the power of visibility with our comprehensive Google Maps SEO service. We optimize your website to climb search rankings and attract organic traffic. Drive growth and reach your audience effectively with our tailored SEO solutions.
Map Ranking Territory Expansion
People search on Google for businesses like yours every single day, but they may not find you if they are more than 10 miles away. Map Ranking will help you rank higher, and in more cities around you so that you can capture more new customers with our Google Maps SEO (local SEO) services.
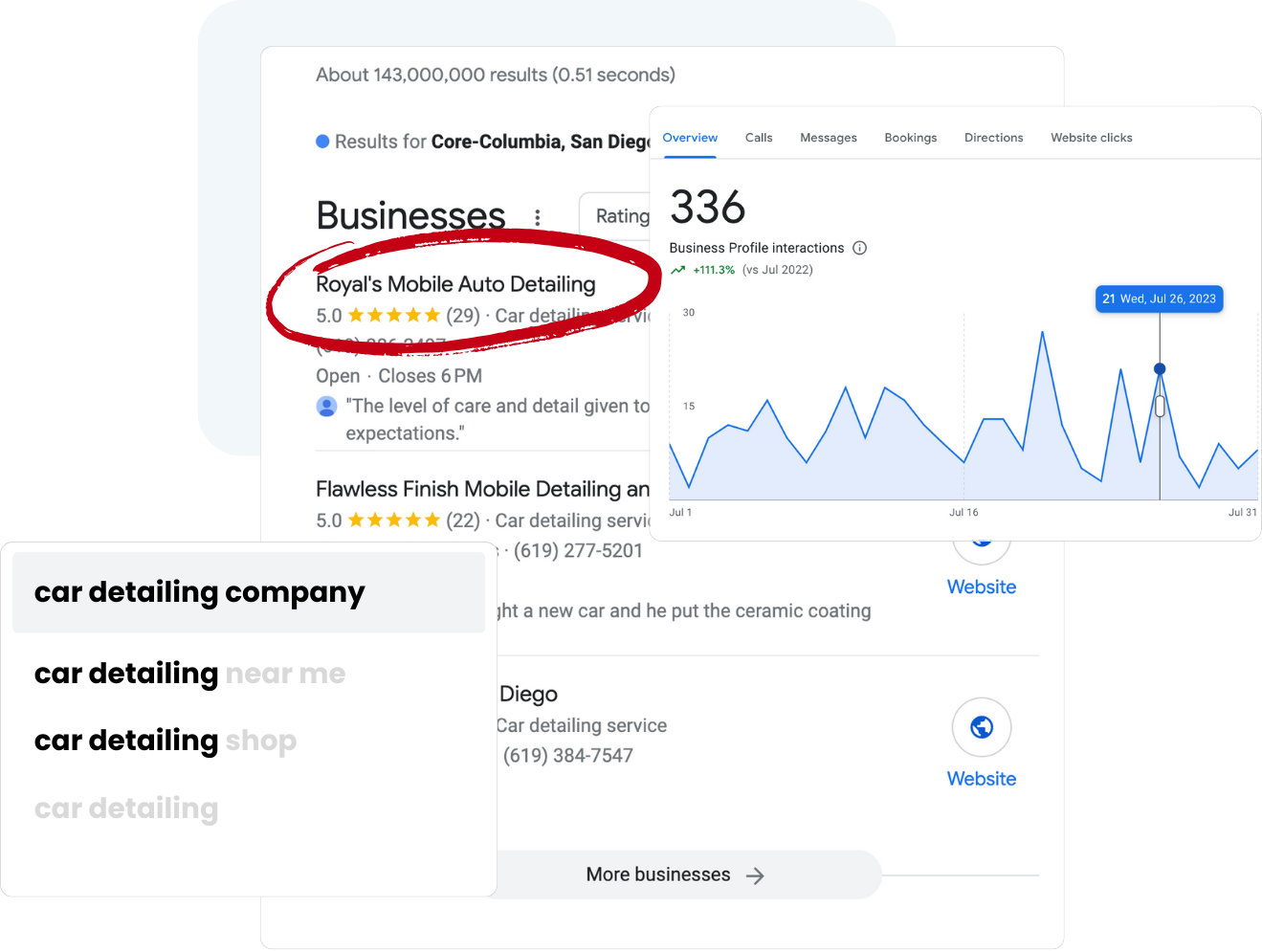
Why Choosing
Map Ranking
Map Ranking’s local SEO and client management software has everything you need to succeed on your own! Plus, we are here to help when you are ready to grow or too busy running a thriving business to handle marketing solo.

MOBILE APP
Access your CRM on the go, manage contacts, and stay connected with customers using our user-friendly mobile app.

Call Tracking
Monitor and analyze calls to understand customer interactions, improving communication and enhancing service quality.
Missed Call Text Back
Automatically send a text message to callers you missed, ensuring no customer inquiry goes unanswered.
Booking & Appointments
Easily schedule and manage appointments, enhancing efficiency and providing a seamless booking experience for your clients.
Live Website Chat
Engage with website visitors in real-time, answering queries instantly and fostering a proactive customer support approach.

Review Generation
Make leaving a review for your business easy, contributing to a positive online reputation for your business.
No contracts! Cancel Any time
Google Maps
Map Ranking Results Guaranteed
Try Map Ranking risk-free and see a boost in rankings and clients or get 100% your money back!
30 days money back guaranteed.